Blockchain Explained – what it is and what it does
Content
– The Vision of Blockchain
– How Does Blockchain Work?
– The Evolution of Blockchain
– Potential Applications of Blockchain Technology
• Blockchain in the Supply Chain
• Blockchain and Smart Cities
• Blockchain and Electronic Healthcare Records
• Blockchain and the Internet-of-Things
– Blockchains are Decentralized, Right?
• Sources of Centralization
• Summary of Potential Vulnerabilities
A blockchain is a decentralized ledger of records of transactions (called blocks) across a peer-to-peer network where participants stay anonymous. In other words, blockchains are networks of physical computers that work together to form a single virtual computer. It’s called a chain because changes can be made only by adding new information to the end – which means that each new transaction grows the chain.
Although a blockchain conceptually serves the same purpose as a traditional database, the approach to data storage used by blockchain is very different. In a blockchain, the data is not stored centrally but shared on a network of computers that all run on a unique software that ensures that all data remains identical and synchronized across all devices. The data in a blockchain is secured by using cryptography.
In 2008, the blockchain concept was introduced by Satoshi Nakamoto in a whitepaper (pdf) as a core component to support transactions of Bitcoin. As the technology that powers cryptocurrencies like bitcoin, blockchains are associated with volatile and (as yet) largely unregulated financial trade, but they are also about more than money. A blockchain could also be a programmable system for secure digital ownership and greater transparency of trade, even between strangers.
Even though technical challenges such as the long-term security, sustainability, stability, scalability and transaction speed of blockchain applications are still being resolved, nevertheless these nascent technologies are starting to be implemented within industry and governments and also increasingly the broader public as tools for digital value creation and trade.
The Vision of Blockchain
For visionaries, blockchain technology will enable a world in which contracts are embedded in digital code and stored in transparent, shared databases, where they are protected from deletion, tampering, and revision. Every agreement, every process, every task, and every payment would have a digital record and signature that could be identified, validated, stored, and shared.
Blockchain can also be programmed with embedded instructions, such as if-else and if-then statements, to carry out actions when certain conditions are met. These instructions can be used to program ‘smart contracts’, which link the information in a blockchain to consequences (e.g., transfer penalty fees) when the agreed terms are not met.
Intermediaries like lawyers, brokers, and bankers might no longer be necessary. Individuals, organizations, machines, and algorithms would freely transact and interact with one another with little friction. This is the immense potential of blockchain – many years in the future. Read this excellent Harvard Business Review article about the transformative power of blockchain.
How Does Blockchain Work?
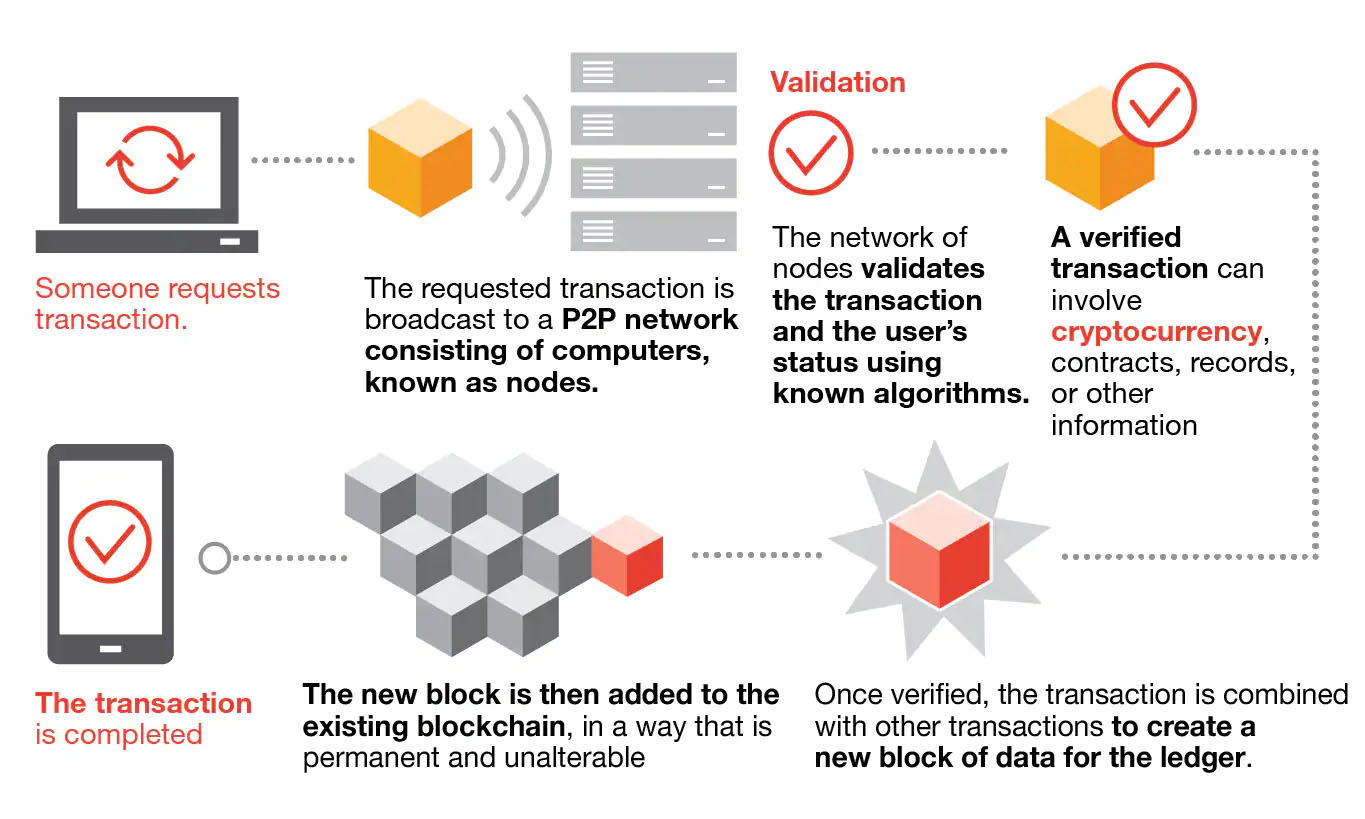
Each new block contains a set of new transactions that reference the entire history of previous transactions in the chain. The information about every transaction ever completed in blockchain is shared and available to all nodes (i.e. users). That means blockchain technically makes everyone the authority – every node in the peer-to-peer network keeps track of whole records in an irreversible tree structure chain to ensure the integrity in a tamper-resistant way.
For example, Bitcoin stores all transactions across the network every ten minutes or so in a single, newly formed block. After the new block is verified (in a process called Bitcoin mining), it is then added to the previous one to form a chain and it is added to every node's copy simultaneously.
Each node on a blockchain has a unique 30-plus-character alphanumeric address that identifies it. Users can choose to remain anonymous or provide proof of their identity to others. Transactions occur directly between blockchain addresses. No third party is in control of the transactions and data; nor is such a central clearing authority required.
Blockchain transactions are irreversible. Once a transaction is entered in the database and the accounts are updated, the records cannot be altered, because they’re linked to every transaction record that came before them. Various computational algorithms and approaches are deployed to ensure that the recording on the database is permanent, chronologically ordered, and available to all others on the network.
In general, blockchain functions in the following steps:
1) A blockchain user creates a new transaction which other stakeholders in the blockchain will be alerted about.
2) The transaction information is propagated to each stakeholder in the blockchain over a period of time.
3) The stakeholders determine the validity of the transaction request. If the request is deemed valid, then the block will become a part of the blockchain.
Based on the blockchain technology characteristics, a blockchain system’s infrastructure model contains mainly two basic layers: the implementation and application layers.
The application layer consists of an API and front end. The implementation layer is further subdivided into four layers: a data layer, network layer, consensus layer, and incentive layer.
The data layer deals with data storage design, digital signatures, and so forth. The next layer, the network layer, deals with peer-to-peer communication. The consensus layer deals with the consensus mechanisms such as Proof-of-Work (PoW) and Proof-of-Stake (PoS); it takes care of how the data is sent and verified among the nodes. This layer is also sometimes referred to as the mining layer. The incentive layer is responsible for linking the blocks with their hash and making sure the blocks are arranged appropriately.

An additional layer, the Compute Interface, allows blockchains to offer more functionality. Practically, a blockchain stores a state consisting for instance of all the transactions that have been made by users, thereby allowing the calculation of each user’s balance. However, for more advanced applications complex states need to be stored, which are updated dynamically using distributed computing, e.g., states that shift from one to another once specific criteria are met. This requirement has given rise to smart contracts, which use nodes of the blockchain to execute the terms of a contract.
Finally, the Governance layer extends the blockchain architecture to cover the human interactions taking place in the physical world. Blockchain governance deals with how these diverse actors come together to produce, maintain, or change the inputs that make up a blockchain.
Proof-of-Work, the most well-known consensus mechanism, requires solving an extremely complicated mathematical problem like finding hashes with specific patterns, e.g., a leading number of zeroes, to ensure authentication and verify a transaction.
Instead of splitting blocks across proportionally to the relative hash rates of miners (i.e., their mining power), Proof-of-Stake protocols split stake blocks proportionally to the current wealth of miners. This way, the selection is fairer and prevents the wealthiest participant from dominating the network. Many blockchains, such as Ethereum, are gradually shifting to PoS due to the significant decrease in power consumption and improved scalability.
Potential applications for blockchain can include fund transfers, settling trades, voting systems, anti-counterfeiting, supply chain security, medical records, smart contracts, and many other issues.
The Evolution of Blockchain
Blockchain technology was first used when the Bitcoin cryptocurrency was introduced. This took place on January 3, 2009, when Nakamoto mined the starting block of the chain, known as the genesis block. To this day, Bitcoin is still the most commonly used application using blockchain technology.
Based on the intended audience, three generations of blockchains can be distinguished:
Blockchain 1.0 (digital currency), which includes applications enabling digital cryptocurrency transactions;
Blockchain 2.0 (digital finance), which includes smart contracts and a set of applications extending beyond cryptocurrency transactions; and
Blockchain 3.0 (digital society), which includes applications in areas beyond the previous two versions, such as government, health, science and IoT.
Blockchain 1.0 took a few years to mature starting from 2009, Blockchain 2.0 and 3.0 have emerged almost in parallel in an explosive manner around 2015.
Potential Applications of Blockchain Technology
Decentralized applications running on blockchain are the cornerstone of web3, the next wave of websites and apps built on decentralized technology. NFTs (non-fungible tokens), which are a rapidly growing web3 area, also rely on smart contract based blockchain platforms.
At the moment, cryptocurrencies represent a considerable percentage of the existing blockchain networks, often leading to a differentiation of blockchain applications into just financial and non-financial ones. Others classify them according to blockchain versions (i.e., 1.0, 2.0 and 3.0).
However, considering the actual and forthcoming heterogeneity of blockchain solutions, a more comprehensive and in-depth classification of blockchain-based applications is called for, graphically represented below:
Let’s look at some examples in more detail.
Blockchain in the Supply Chain
Blockchain-based supply chains enable each stakeholder to record price, date, location, quality, certification, and other relevant information to more effectively manage information across supply chain.
The availability of this information within blockchain can increase traceability of material supply chain, lower losses from counterfeit and gray market, improve visibility and compliance over outsourced contract manufacturing, and potentially enhance an organization's position as a leader in responsible manufacturing.
For instance, Bext360, a startup, is using blockchain as part of an effort to increase supply chain transparency in the second-largest traded commodity in the world—coffee beans. The company is using a distributed, decentralized protocol for real-time mobile transactions, recording data about the transactions and allowing all involved parties to access the record of payments at any time. The system increases transparency as the coffee beans progress through the supply chain and helps to ensure farmers receive proper fair-trade payments.
Blockchain and Electronic Healthcare Records
Medical data are always vulnerable to different security threats such as data loss, data leaks, malicious tampering, and other issues. One proposed solution to this problem is a secure and efficient blockchain-based framework for the management of electronic healthcare records of all stakeholders of the health sector, that is, hospitals, doctors, patients, and other third-party administrators with required permissions.
Researchers have already proposed a permissioned blockchain-based framework using Hyperledger Fabric (HLF) is proposed, which provides secure storage, sharing, and querying of electronic health records (read more: Blockchain-based framework for secured storage, sharing, and querying of electronic healthcare records).
Blockchain and Smart Cities
A smart city is an infrastructure framework that addresses the growing urbanization challenges by embracing integrated and automated information and communication technologies to help optimize all city operations, help achieve sustainability goals and better quality of life for its citizens (read more here in our primer on smart cities)
Blockchain and the Internet-of-Things
There are many kinds of Internet-of-Things (IoT) business platforms that support IoT networks and service requirements. The traditional IoT business platform is the centralized working model. The platform is deployed in a single location on the system side and managed by a single vendor providing centralized services.
However, nowadays, with the rapid growth of IoT, more and more of the infrastructure for storing and processing data is being shifted away from data centers and towards operating directly on edge devices.
Edge computing allows resources and applications to be distributed in a decentralized infrastructure outside the cloud. Two main benefits of edge computing are improved performance and reduced operational costs. Data collection in edge computing is done locally. Since transferring large amounts of data can be complicated, edge computing brings data close to the machine, cutting out the transmission time.
However, because they are widely decentralized, these edge devices face serious risks in the security of data and transactions. Blockchain can solve many issues with IoT.

Blockchains are Decentralized, Right?
While there are many different types of Distributed Ledger Technology (DLT), each built with fundamentally different design decisions, the overarching value proposition of DLT and blockchains is that they can operate securely without any centralized control. The cryptographic primitives that enable blockchains are, by this point, quite robust, and it is often taken for granted that these primitives enable blockchains to be immutable (not susceptible to change).
However, there are several examples of how that immutability can be broken not by exploiting cryptographic vulnerabilities but instead by subverting the properties of a blockchain’s implementations, networking, and consensus protocol. For instance, a subset of participants can garner excessive, centralized control over the entire system.
Sources of Centralization
There are several ways in which control of a DLT can be centralized:
Authoritative centrality: What is the minimum number of entities necessary to disrupt the system? This number is called the Nakamoto coefficient, and the closer this value is to one, the more centralized the system. This is also often referred to as “Governance Centrality”.
Consensus centrality: Similar to authoritative centrality, to what extent is the source of consensus (e.g., proof-of-work [PoW]) centralized? Does a single entity (like a mining pool) control an undue amount of the network’s hashing power?
Motivational centrality: How are participants disincentivized from acting maliciously (e.g., posting malformed or incorrect data)? To what extent are these incentives centrally controlled? How, if at all, can the rights of a malicious participant be revoked?
Topological centrality: How resistant is the consensus network to disruption? Is there a subset of nodes that form a vital bridge in the network, without which the network would become bifurcated?
Network centrality: Are the nodes sufficiently geographically dispersed such that they are uniformly distributed across the internet? What would happen if a malicious internet service provider (ISP) or nation-state decided to block or filter all DLT traffic?
Software centrality: To what extent is the safety of the DLT dependent on the security of the software on which it runs? Any bug in the software (either inadvertent or intentional) could invalidate the invariants of the DLT, e.g., breaking immutability. If there is ambiguity in the DLT’s specification, two independently developed software clients might disagree, causing a fork in the blockchain. An upstream vulnerability in a dependency shared by the two clients can similarly affect their operation.
Summary of Potential Vulnerabilities
● The challenge with using a blockchain is that one has to either (a) accept its immutability and trust that its programmers did not introduce a bug, or (b) permit upgradeable contracts or off-chain code that share the same trust issues as a centralized approach.
● Every widely used blockchain has a privileged set of entities that can modify the semantics of the blockchain to potentially change past transactions.
● The number of entities sufficient to disrupt a blockchain is relatively low: four for Bitcoin, two for Ethereum, and less than a dozen for most PoS networks.
● The vast majority of Bitcoin nodes appear to not participate in mining and node operators face no explicit penalty for dishonesty.
● The standard protocol for coordination within blockchain mining pools, Stratum, is unencrypted and, effectively, unauthenticated.
● When nodes have an out-of-date or incorrect view of the network, this lowers the percentage of the hashrate necessary to execute a standard 51% attack. Moreover, only the nodes operated by mining pools need to be degraded to carry out such an attack. For example, during the first half of 2021 the actual cost of a 51% attack on Bitcoin was closer to 49% of the hashrate.
● For a blockchain to be optimally distributed, there must be a so-called Sybil cost. There is currently no known way to implement Sybil costs in a permissionless blockchain like Bitcoin or Ethereum without employing a centralized trusted third party (TTP). Until a mechanism for enforcing Sybil costs without a TTP is discovered, it will be almost impossible for permissionless blockchains to achieve satisfactory decentralization.
● A dense, possibly non-scale-free, subnetwork of Bitcoin nodes appears to be largely responsible for reaching consensus and communicating with miners—the vast majority of nodes do not meaningfully contribute to the health of the network.
● Bitcoin traffic is unencrypted—any third party on the network route between nodes (e.g., ISPs, Wi-Fi access point operators, or governments) can observe and choose to drop any messages they wish.
● Of all Bitcoin traffic, 60% traverses just three ISPs.
● Tor is now the largest network provider in Bitcoin, routing traffic for about half of Bitcoin’s nodes. Half of these nodes are routed through the Tor network, and the other half are reachable through .onion addresses. The next largest autonomous system (AS)—or network provider—is AS24940 from Germany, constituting only 10% of nodes. A malicious Tor exit node can modify or drop traffic similarly to an ISP.
● Of Bitcoin’s nodes, 21% were running an old version of the Bitcoin Core client that is known to be vulnerable in June of 2021.
● The Ethereum ecosystem has a significant amount of code reuse: 90% of recently deployed Ethereum smart contracts are at least 56% similar to each other.
Check out our SmartWorlder section to read more about smart technologies.